There are many types of so called WAR ROOMS and could define a physical bricks and mortar building or a virtual room distributed across the globe.
Why Room #11? Our playground is in the Cloud but we have both our feet on the ground. Every business is unique and we like to meet our clients face to face ONE ON ONE.
In technology terms it could also be a team gathered, virtually or at a physical location, overseeing the entire lifecycle of your cloud software responsible for the day to day functioning of your business.
It could be a security company monitoring your alarm system with an array of big screens, a help desk managing internal IT Support for a company or a team with a wide range of skills & roles from various disciplines.
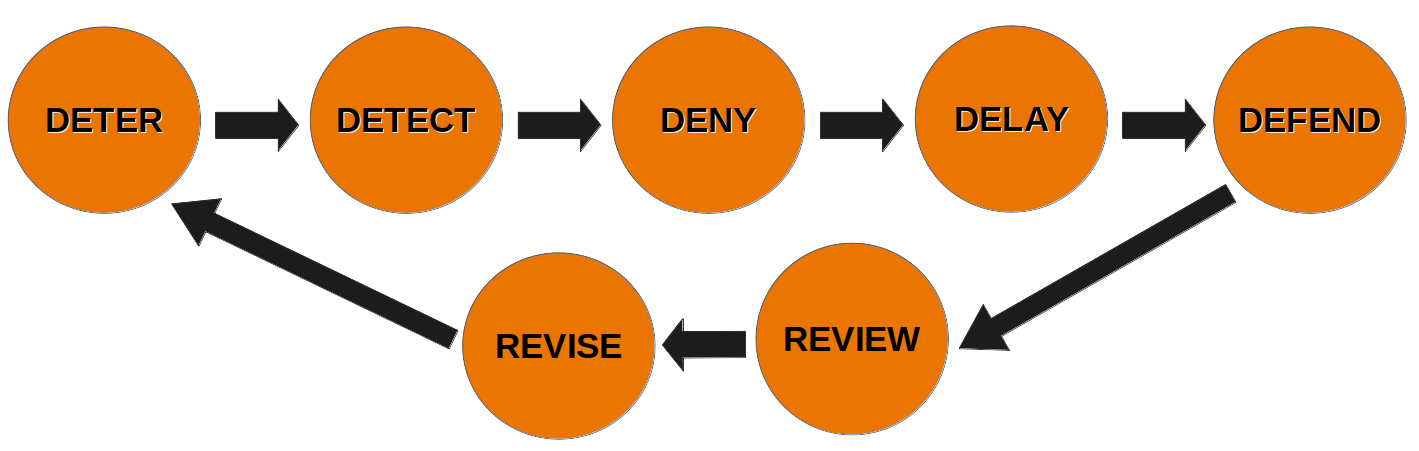
Google defines militaristic as "advocating or pursuing an aggressive military policy; hawkish". That is our style. With a zero tolerance for cyber vagrants, hackers & industrial or commercial spies, physical access to secure and sensitive assets, we follow the well known 5D security principles (Deter, Detect, Deny, Delay and Defend) Embracing a LEAN approach to continuous process improvement, we add REVIEW and REVISE (RR++) to the D5 Access Control Framework.
The DEVSECOPS role defines our Development & Implementation strategy towards our clients and in addition to DevOps Engineering described in the next article we consider:
- DEV: Lean Software Development & Process Improvement.
- SEC: We obviously take Cyber and Physical Security seriously and embrace the ISO 27001 Security Standards.
- OPS: Operational. Compilation and Implementation of Standard Operating Procedures (SOPs)
Almost all aspects of Physical Security has become increasingly dependent on cloud technology. With most modern devices, from security, production machines, refrigeration to home automation devices, appliances & equipment are connected with wireless capabalities and moble remote control capabilities. The Cloud has become a playing field for criminals. Cyber Crime is no longer just a digital threat, society is faced with physical threats of all sorts.
Adding to the typical and well known D5 Access Control Framework (Deter, Detect, Deny, Delay and defend) and bearing in mind the rapidly changing security risk landscape, the measures implemented according to the framework needs continuous REVIEW and REVISION.
The D5RR++ framework is applicable to both physical and cloud security.
Providing custom security solutions for commercial, industrial & private clients.
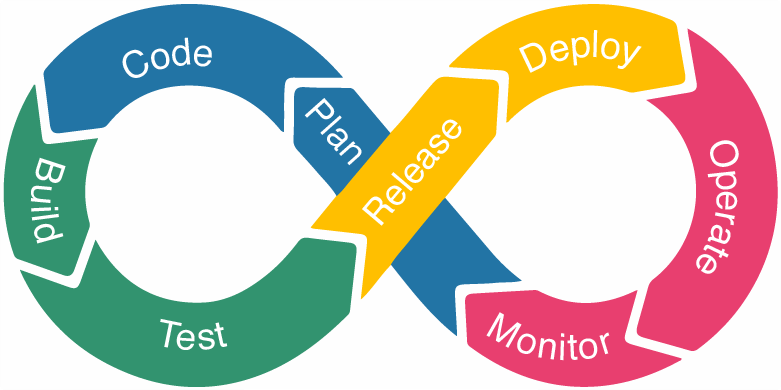
- Analyse and Plan: Your snaglist is as important as your wishlist. Identify the key areas where small process improvement can add value. Never underestimate the input of your staff, the people on the factory floor. Holisiticly look at the entire business but improve one process at a time. Too much change at a time is a recipe for failure.
- Code: Keep it simple. Don't re-invent the wheel.
- Build: Build & deploy the software in an environment matching the production environment
- Test: Running automated test can reduce testing time but also test real world users.
- Release: Introduce the client to the new features. Train them where required
- Deploy: Update the production environment. Beware of possible downtime.
- Operate: Allow the user to use the new feature
- Monitor: Keep an eye on everything from security to the error logs. Get regular feedback from users and system performance.

- An animal that naturally preys on others. "wolves are major predators of small mammals"
- A person who ruthlessly exploits others. "a sexual predator"
- A person harmed, injured, or killed as a result of a crime, accident, or other event or action. "victims of domestic violence"
- A person who is tricked or duped. "the victim of a hoax"
- A person who has come to feel helpless and passive in the face of misfortune or ill-treatment.
- A living creature killed as a religious sacrifice.
Many ethical hackers form groups on the web to combat, track down and expose Predators. SecureMax.Live is part of such a group of hunters tracking down vagrants of all sorts on a global scale.